Secure Your Critical Systems with Recorded HTTPS Access
One portal. Encrypted session replay. Zero Trust control.
Now featuring HTTPS recording, Cloudflare Access orchestration, and ABAC-driven audit intelligence.
Platform Tour
Click to watch the Zero Trust admin experience
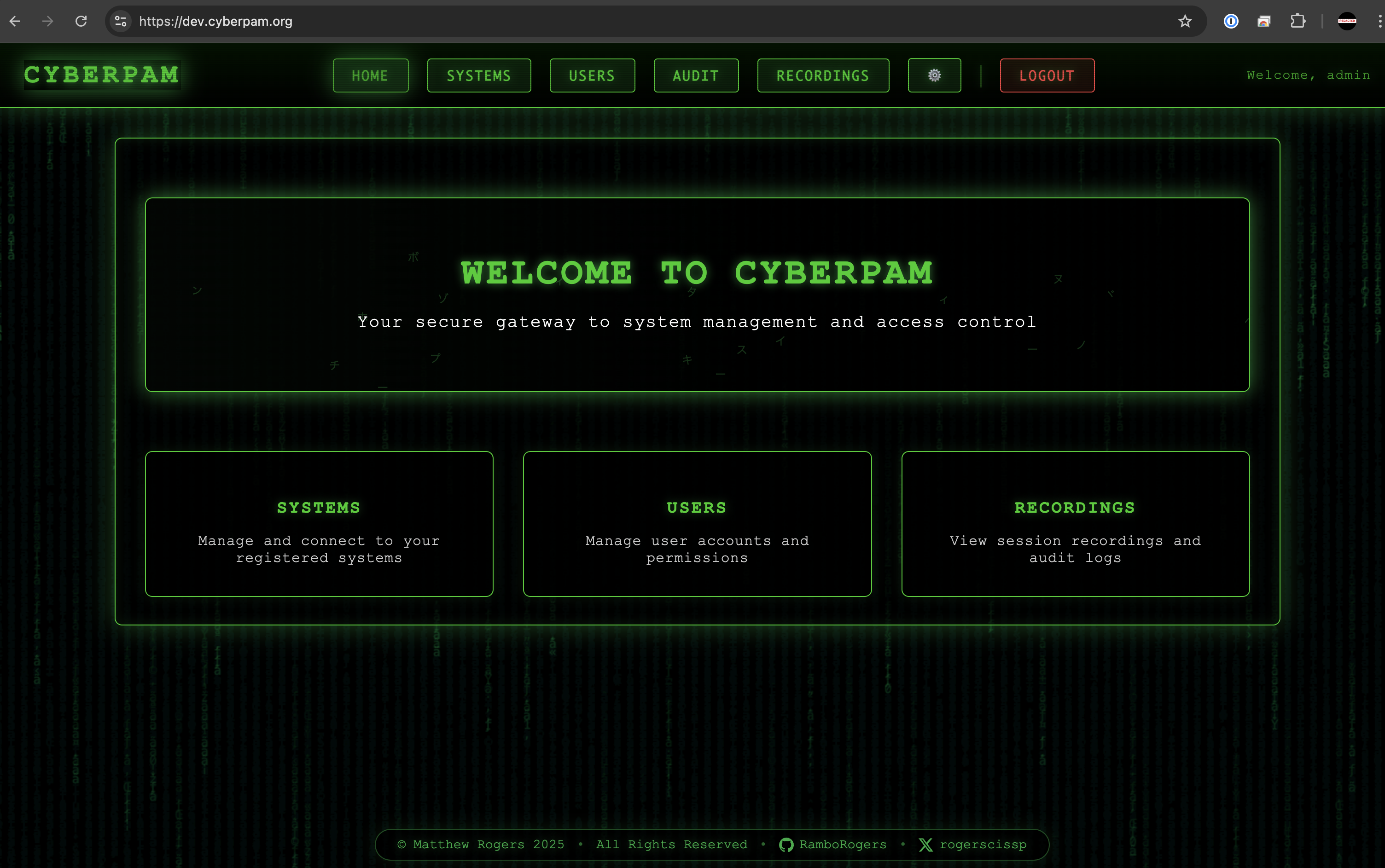
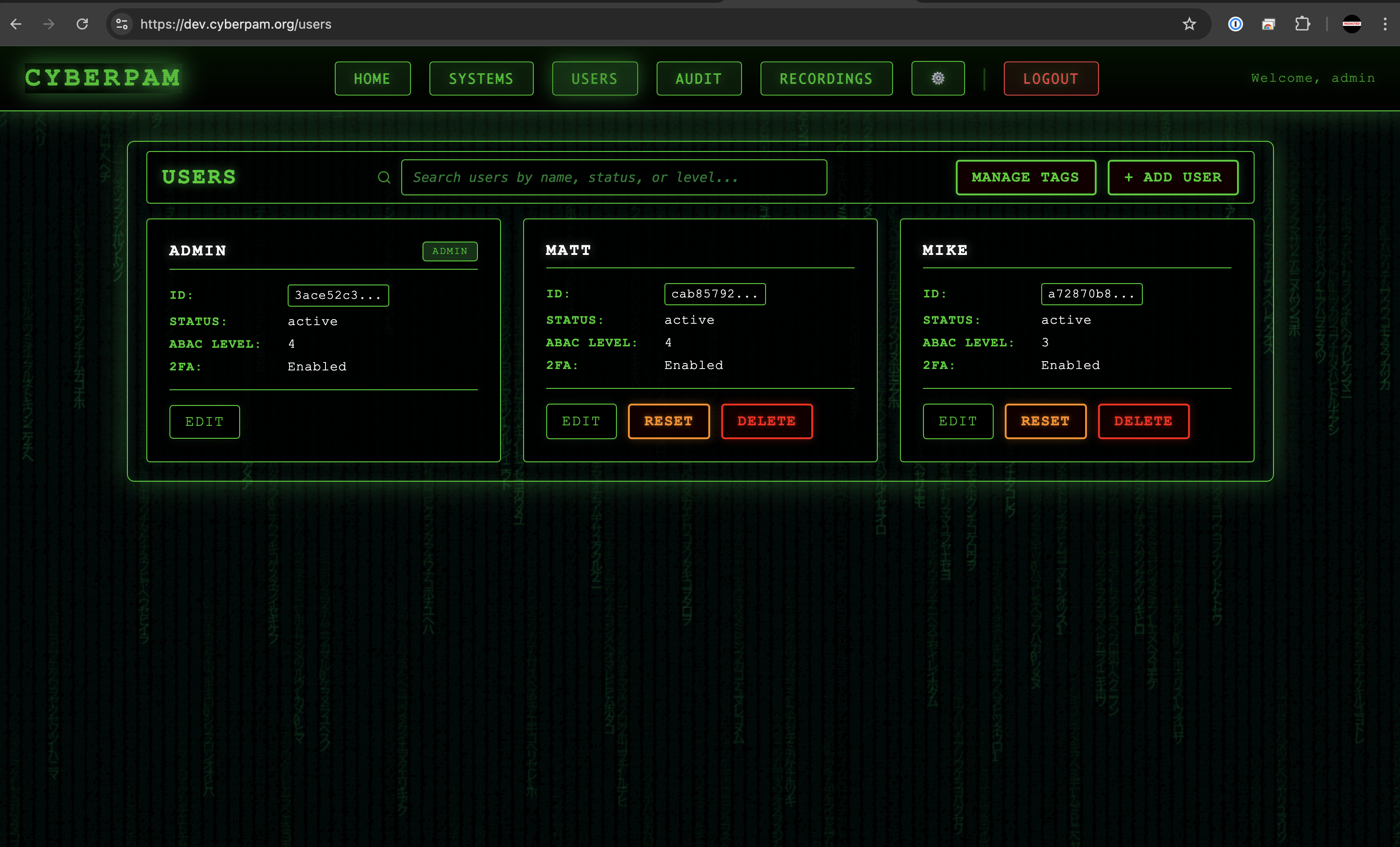
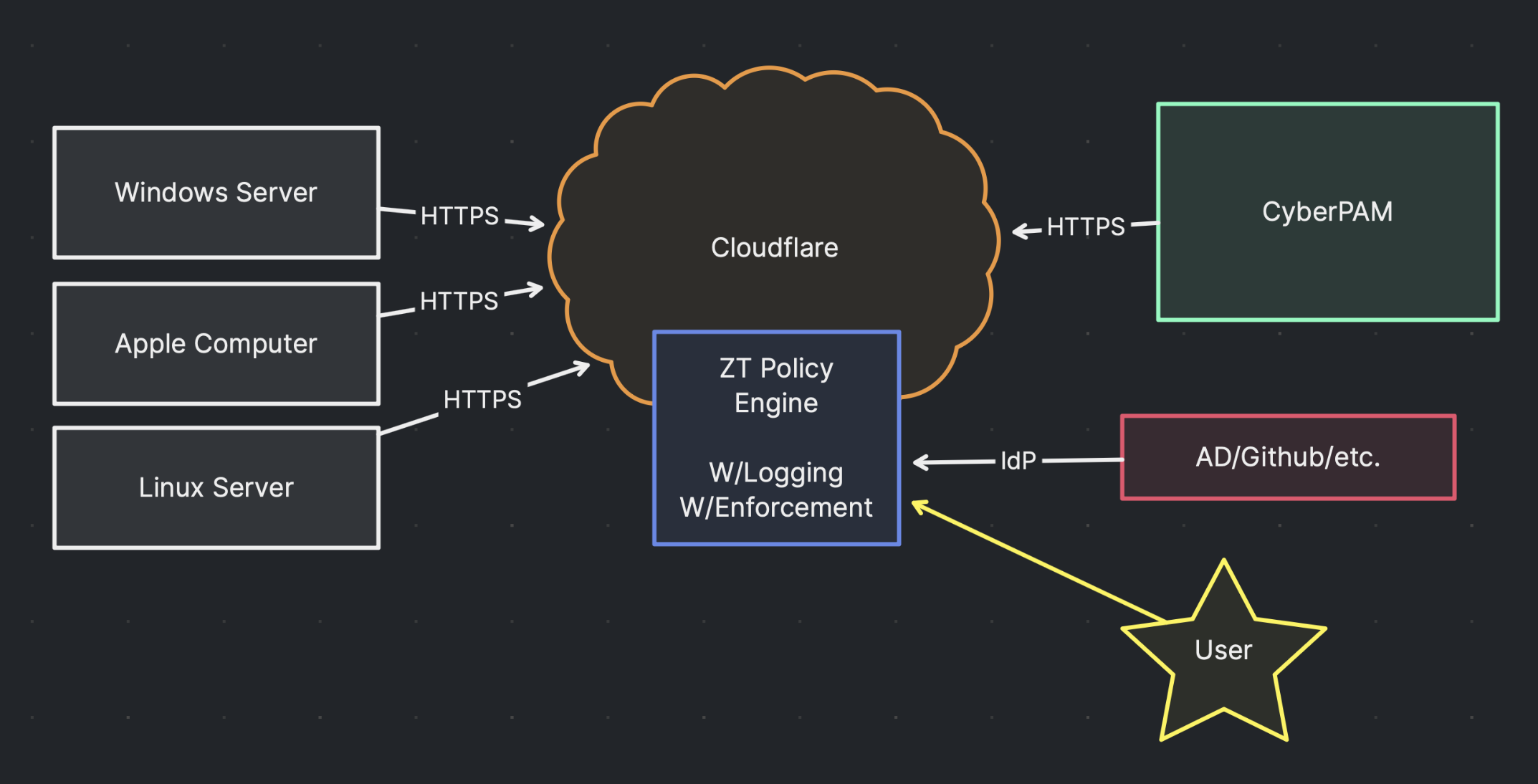
Unified Zero Trust Portal
Provision Cloudflare Access, onboard users, and broker sessions through a single interface.
New · HTTPS Recording
Replay an encrypted privileged browser session
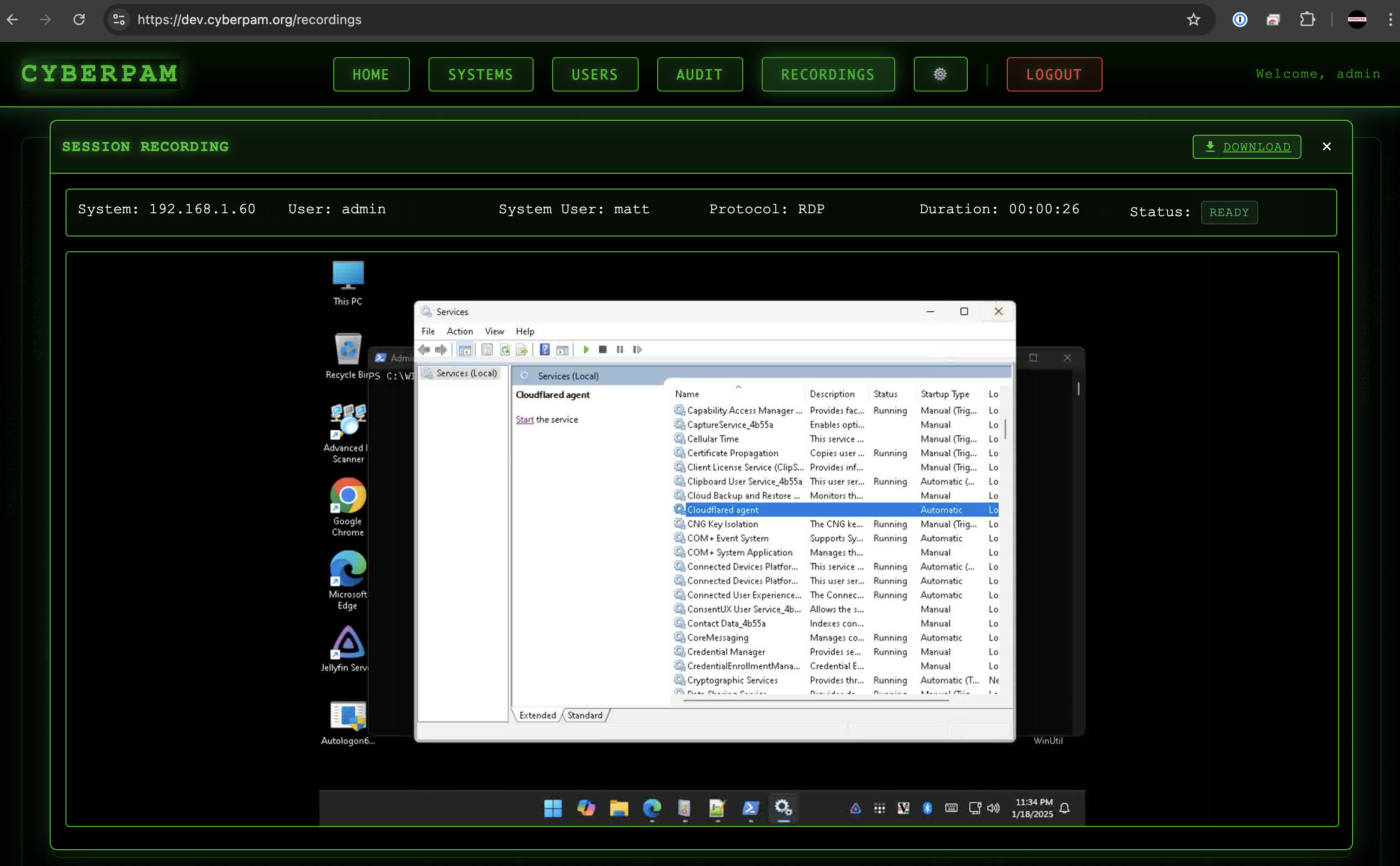
Encrypted HTTPS Session Replay
Showcases deterministic capture of web-based admin activity with ABAC-tagged audit trails and instant playback.
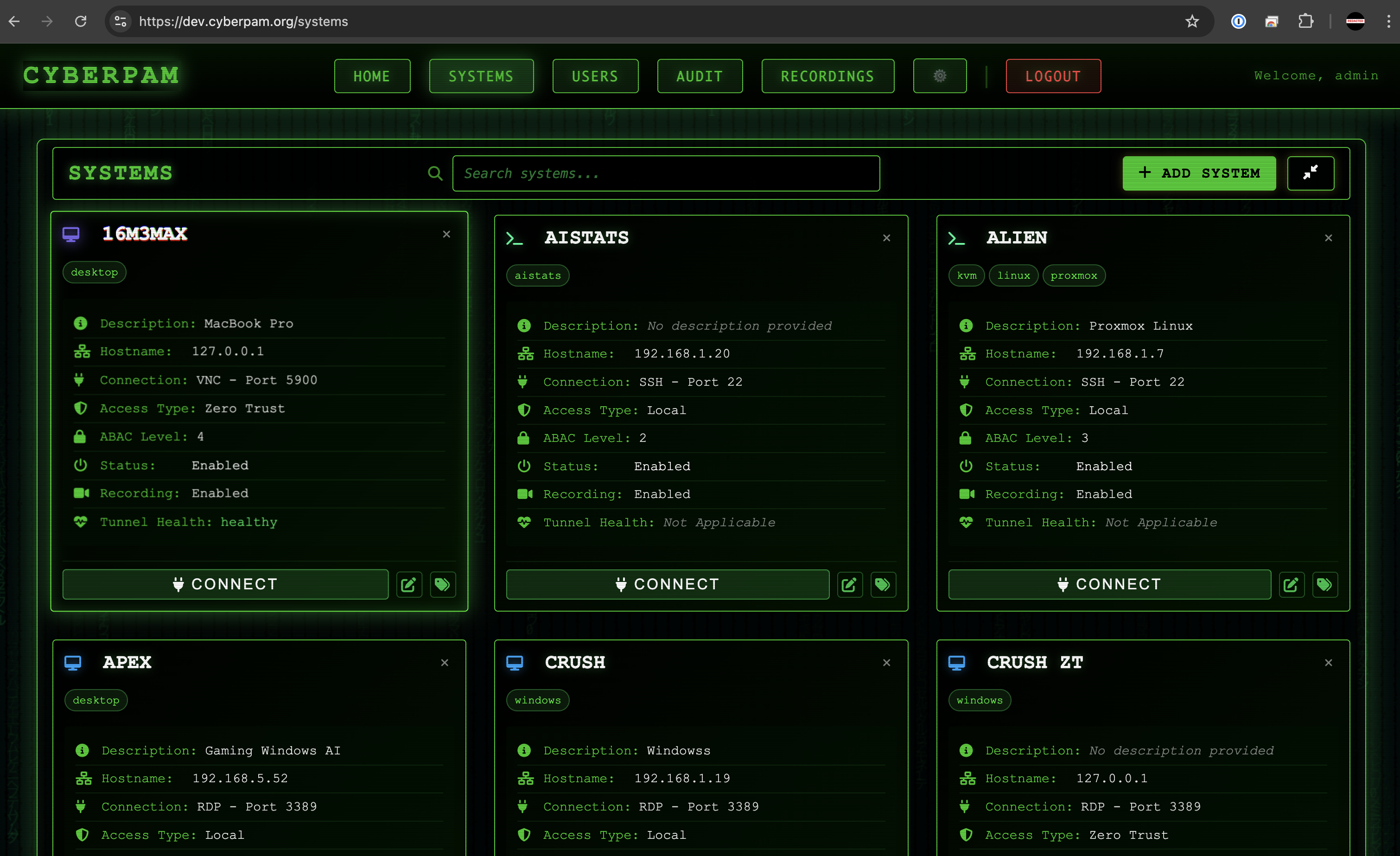
Privileged ZTNA
Broker administrator access through Cloudflare Zero Trust plus CyberPAM session governance.
Protocol Isolation
Convert HTTPS tunnels into RDP or SSH without ever exposing internal ports.
HTTPS Session Replay
Capture encrypted browser sessions with searchable, tamper-evident playback.
Zero Trust Privileged Operations, Verified
CyberPAM orchestrates identity, policy, and session evidence in one hardened portal.
Credential-Free Access
Leverage Cloudflare Access SSO and ephemeral credentials for every privileged launch.
Isolated Admin Pathways
Route sensitive RDP/SSH flows through HTTPS micro-tunnels with protocol isolation.
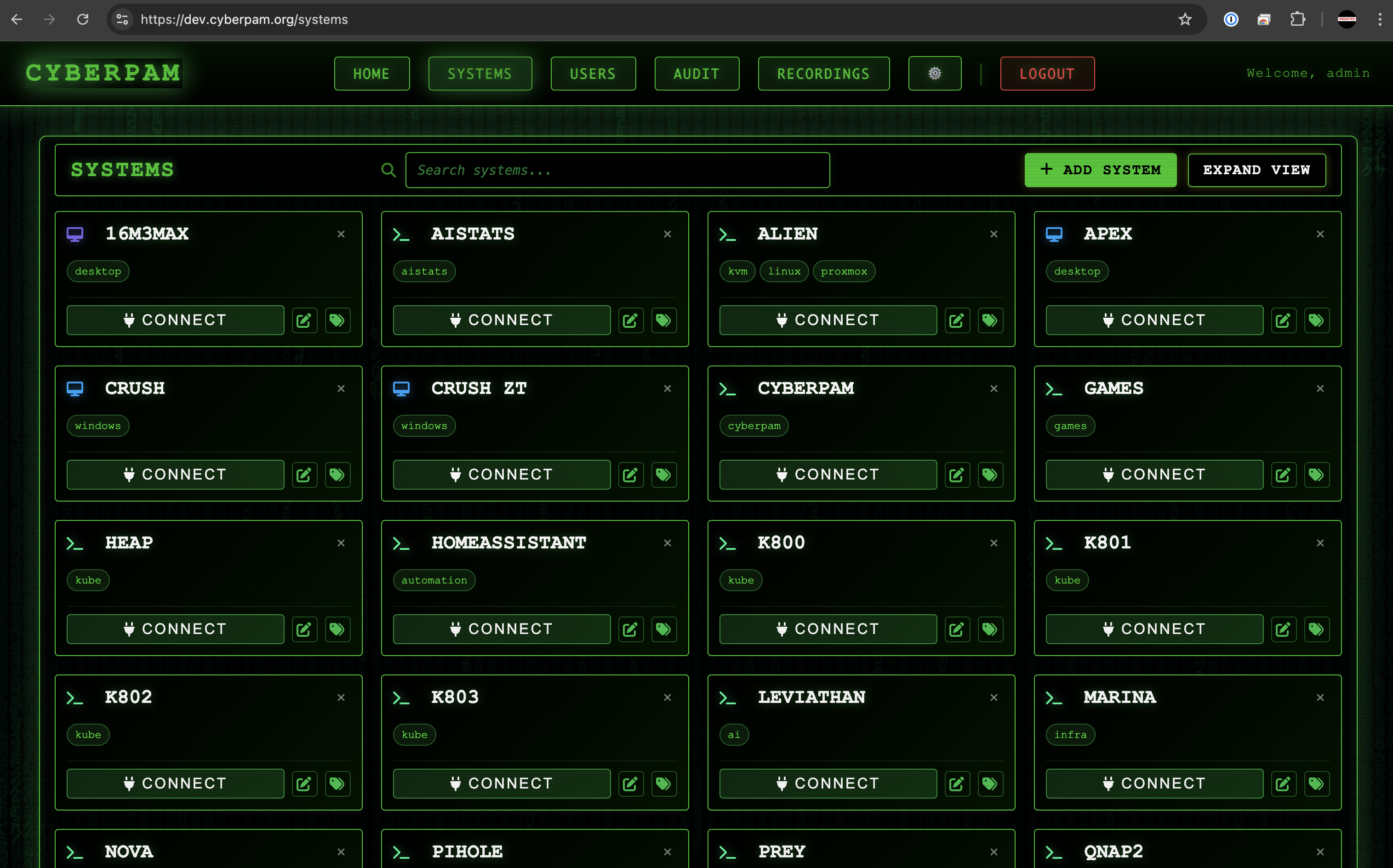
Quick Cluster Access
Deliver bastion-less access to fleets in minutes with automated onboarding.
Ransomware Prevention
Stop lateral movement with continuous verification and forensic session capture.
Secure Cloud Access
Harden browser-based workflows with HTTPS recording and contextual policy.
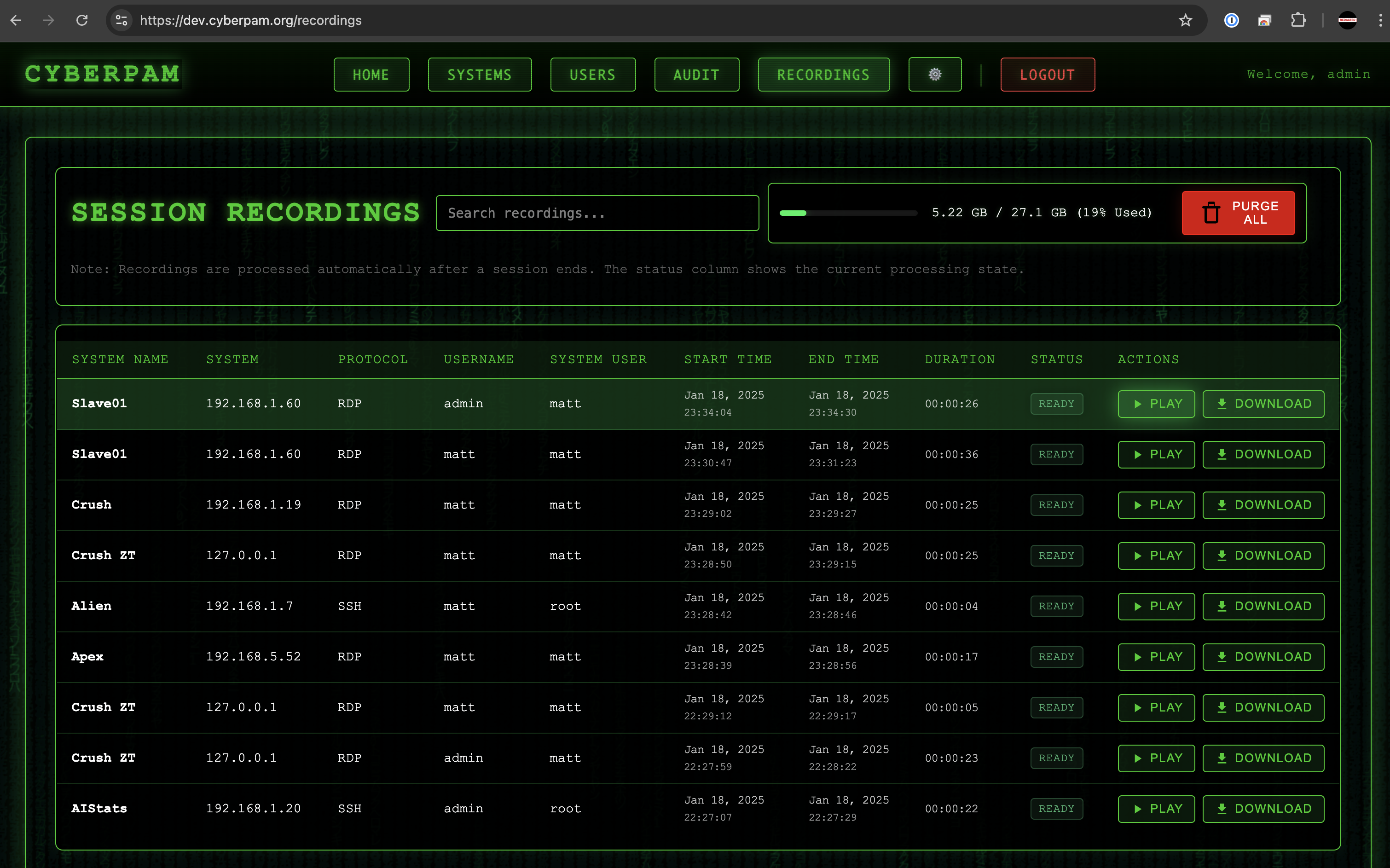
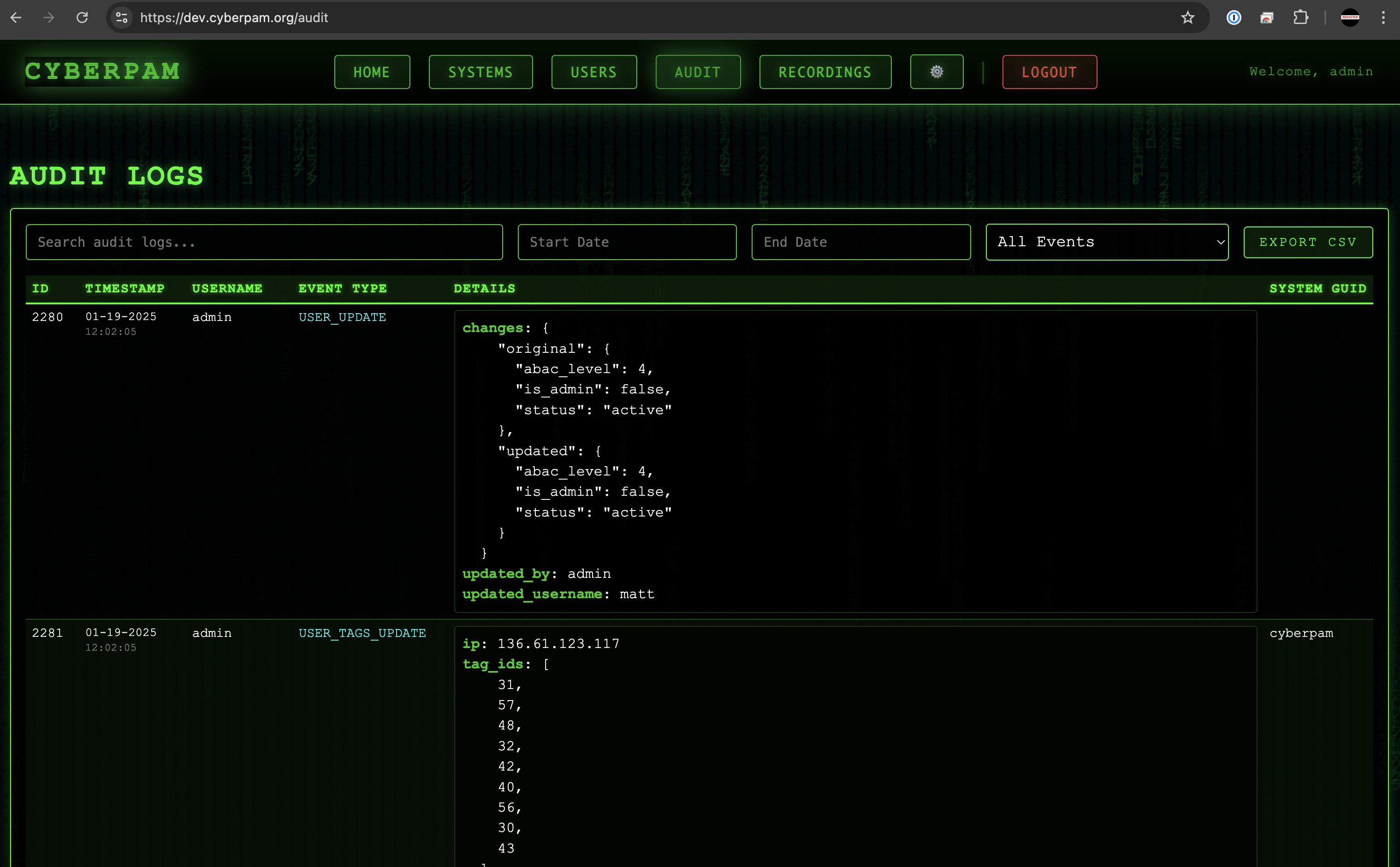
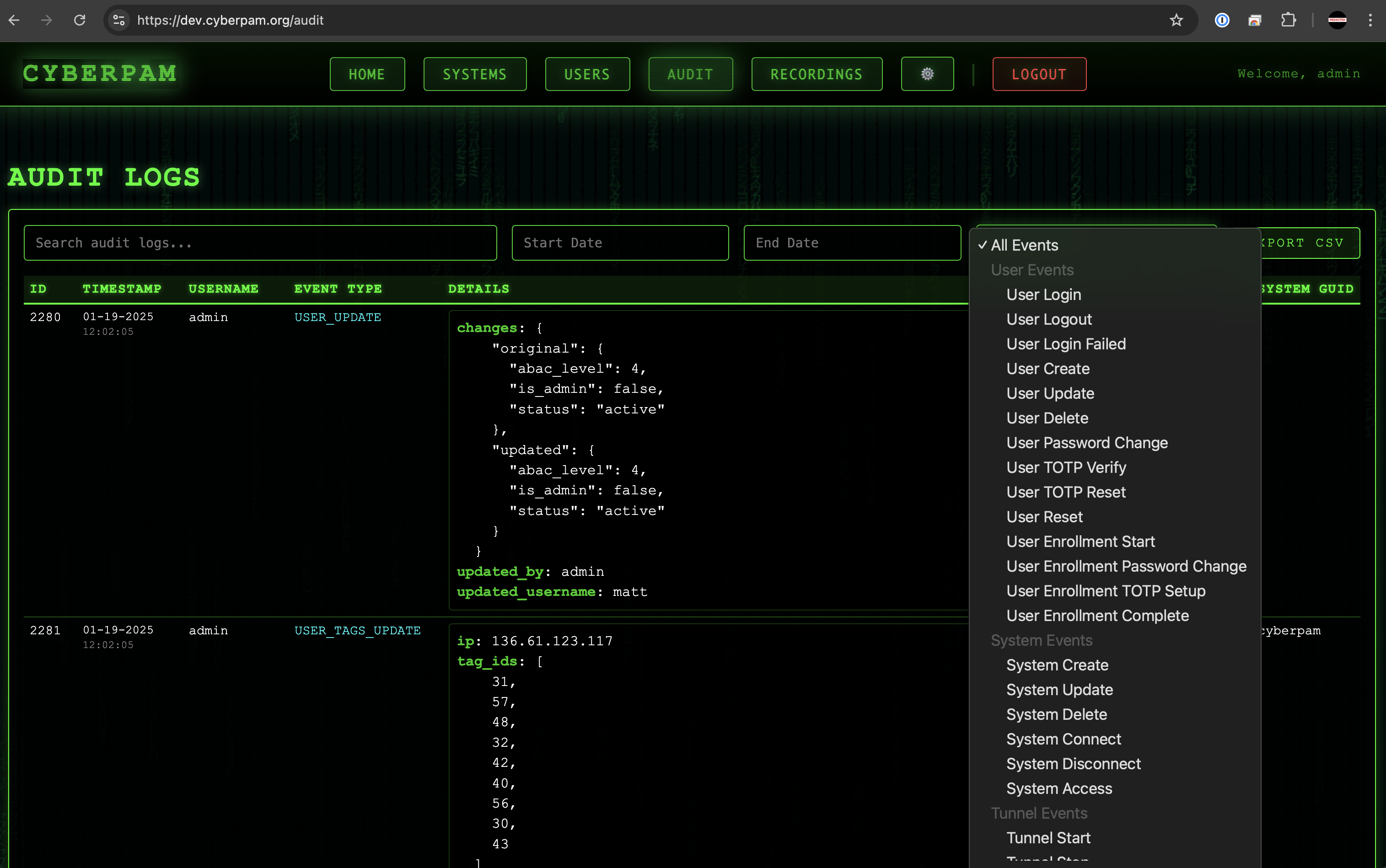
Operational Evidence
Automate ABAC-tagged audit logs and export-ready recordings for every session.
Instant Web Portal
One-click HTTPS portal delivering SSH, RDP, and browser sessions with full replay.
Most Popular